
In this project, I demonstrate how phishing works using a Kali Linux tool called Zphisher, which is only for educational purposes. Zphisher is an open-source phishing tool that offers a wide range of templates that can be customized to suit the attacker’s needs for education purposes.
Zphisher provides a web-based interface that allows attackers to create and host phishing pages on a web server that they can control. These pages can be designed to mimic legitimate websites such as social media platforms, streaming services, or email providers.
Once the phishing page is set up, attackers can send emails or messages containing links to the fake page. When a victim clicks on the link and enters their login credentials or other sensitive information, Zphisher captures it and stores it on the attacker’s server.
I adhered to ethical standards throughout this project and never engaged in illegal or malicious activities. However, as a cybersecurity enthusiast, learning about potential vulnerabilities and attack vectors is crucial to better protect against them.
Disclaimer:
All information, techniques, and tools described in this write-up are for educational purposes only. Use anything in this write-up at your discretion, and I cannot be held responsible for any damages caused to any systems or yourselves legally. Using all tools and techniques described in this write-up for attacking individuals or organizations without their prior consent is highly illegal. You must obey all applicable local, state, and federal laws. I accept no liability and will not be responsible for any misuse or damage caused by using the information herein.
LinkedIn Phishing Link
I ran the bash script in Kali Linux to start Zphisher.

Inside Zphisher. A lot of different options to choose from.

For the first demonstration, I used LinkedIn by inputting the corresponding number.
Typed 14 → pressed Enter.

The Port forwarding service used for this demonstration was Cloudflared.
Typed 02 → pressed Enter.

Typed n for No Custom Port.
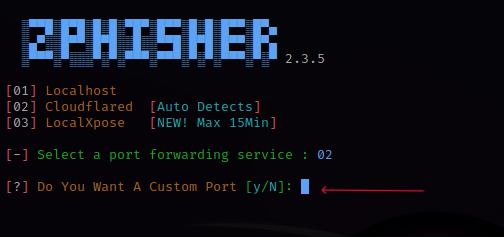

Typed y to change Mask URL. Pressed Enter.

Typed the custom URL: jbtechtesting.com. Pressed Enter.


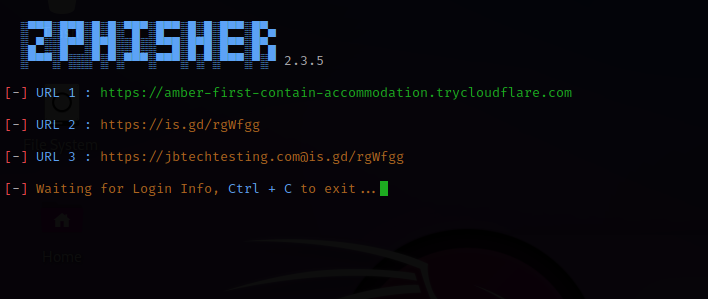
The phishing links were created.

I selected and copied the URL 3 link.

I opened a new web browser and pasted the phishing URL, which sent me to a LinkedIn login page.
I clicked Yes to proceed with the demonstration.

The URL 3 phishing link took us to a LinkedIn login page where we could enter credentials.
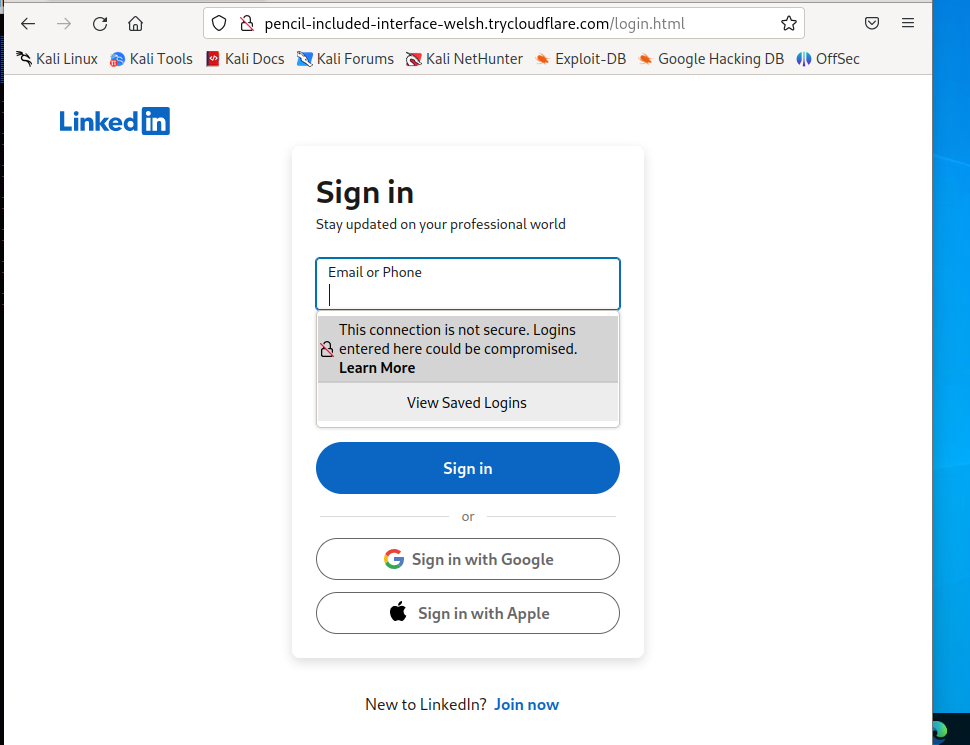
Note: The username is jbthepentester@tech.com, and the password is Demonstration.

I clicked Don’t save.

After submitting the username and password, it will appear not to have done anything from the LinkedIn page. Still, it was re-routed to the actual LinkedIn login page, and the user will most likely give the login another try.
Back in Zphisher, we have the results from the first login attempt to the fake LinkedIn page. We can see that we have the Victim’s IP address, account username, and password.

Another way to look at it is to:
CD into the ZPhisher directory → CD into the zphisher tool.
Typed ls → pressed Enter.

Typed cdauth → pressed Enter.

Typed ls → pressed Enter.

Typed cat usernames.dat → pressed Enter.
We can see LinkedIn Username: jbthepentester@tech.com and Pass: Demonstration.

**
Instagram Phishing Link**
For the second demonstration, I used Instagram.
I chose option 02 → pressed Enter.

I chose option 03 → pressed Enter. This link entices the victim to gain 1000 followers by clicking it and logging in.

I chose 02 → pressed Enter.

I typed N for NoCustom Port.


I typed y to mask the URL and for the custom URL: jbtechtesting.com.

I selected and copied the URL 3 link.
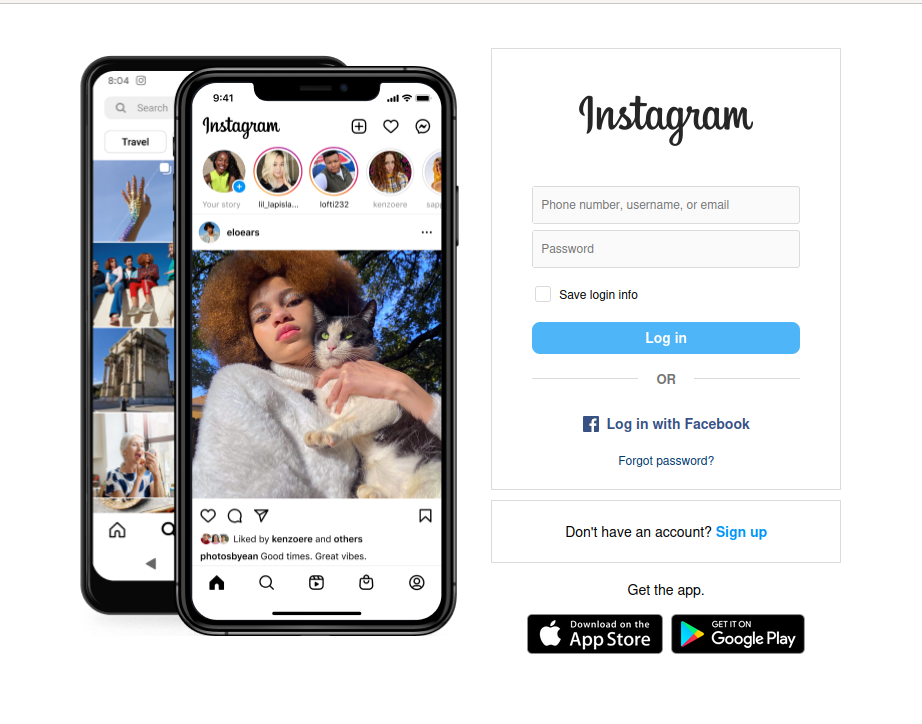
I opened a new web browser and pasted the URL 3 link, which took me to the Free Instagram Followers Trial login page.

Note: Username jbtechtesting@tech.com and password Demonstration2.
I clicked Submit Query, which redirected me to the real Instagram login page.

Now back in Zphisher, we have the results from the Instagram login attempt. We can see that we have the Victim’s IP address, Instagram account username, and password.

ls → cd auth → ls → cat usernames.dat
We can see Instagram Username:jbtechtesting@tech.com and Pass: Demonstration2.

Zphisher is a powerful tool used by security researchers, ethical hackers, and penetration testers to test the security of an organization’s systems and educate employees about the dangers of phishing attacks and malicious actors.
Thank You For Reading This Information And Giving Your Precious Time On This.....
_________________Warning________________
"This Blog Is Only For Educational Purpose Please Don't Use This Knowledge ToHarm Anyone'sPrivacy And Life. By Teaching This Trick We Are Not Responsible For Your Illigal Activity On This Knowledge"